
We are sitting at the intersection of cybersecurity and artificial intelligence in the enterprise, and there is much to know and do. Our goal is not just to keep you updated with the latest AI, cybersecurity, and other crucial tech trends and breakthroughs that may matter to you, but also to feed your curiosity.
Thanks for being part of our fantastic community!
In this edition:
Did You Know - Value of Rapid Patching
Article - What Every Leader Needs to Know About the Velocity of Patching
Cybersecurity News & Bytes
AI Power Prompt
Social Media Image of the Week
Did You Know - Value of Rapid Patching
Did you know unpatched software was exploited in approximately 25 % of reported breaches in 2024, emphasizing the critical need for timely patch deployment? Source: SBS Cybersecurity Blog
Did you know organizations that reduced their patch deployment window from 30 days to 7 days saw an average 34 % reduction in successful breach attempts? Source: Trend Micro’s 2025 Cyber Risk Report
Did you know 78 % of successful breaches exploited vulnerabilities for which patches were already available but not yet applied? Source: Trend Micro’s 2025 Cyber Risk Report
Did you know if an enterprise patched immediately upon vendor release, it would be 4.9 × less likely to be compromised compared to waiting one month, and 9.1 × less likely if compared to a three-month delay? Source: arXiv
Did you know automated patching is used by 76 % of organizations, and 46 % use live patching, helping reduce disruption while maintaining rapid response? Source: arXiv
Did you know according to the NSA’s Top 10 Cybersecurity Mitigation Strategies, rapid and thorough patching is paramount, and without it, attackers can strike within the defender’s patch cycle? Source: NSA

What Every Leader Needs to Know About the Velocity of Security Updates
Here are seven important things you need to know
In today’s threat environment, the speed at which your organization applies security updates—your patch velocity—can mean the difference between an uneventful week and a public crisis. Attackers are now exploiting newly disclosed vulnerabilities within hours. Many companies still take weeks to close the gap, leaving a dangerous window for intrusion.
Treating patch speed as a technical afterthought is no longer acceptable. It’s a business resilience issue that belongs in the boardroom. Here are seven ways leaders can accelerate patching and reduce exposure.
Make it a leadership priority
Discuss patch timelines alongside other business risks. When executives track patch velocity as a performance metric, it sends a clear signal across the organization that delays are not an option.Know what you have
You can’t patch systems you can’t see. Maintain real-time asset inventories so that when a new critical flaw is announced, you instantly know which machines are affected and can respond without hesitation.Focus on the worst first
Not every patch carries the same urgency. Use risk-based prioritization to identify and remediate vulnerabilities most likely to be exploited, especially on internet-facing or mission-critical systems.Automate where possible
Manual patching is slow and error-prone. Invest in tools that scan for missing updates, deploy patches automatically, and orchestrate the process across your environment. Automation frees your team from repetitive tasks and shortens the time from release to protection.Don’t let downtime fears stall action
It’s tempting to delay updates to avoid short outages. But a brief planned disruption is far less damaging than the days or weeks of downtime caused by a breach. Encourage a mindset that values prevention over perfect uptime.Align teams around the goal
Fast patching requires coordination between IT, security, compliance, and business units. Build a culture where urgent updates are understood, accepted, and supported across departments. Clear communication prevents bottlenecks.Measure and improve continuously
Track how long it takes to deploy critical updates and set internal targets. Review delays, identify root causes, and refine the process. Over time, you can transform urgent patching from a scramble into a routine.
Every extra day before patching is really just another day of unnecessary risk. By making patch velocity an executive priority and embedding these seven practices into daily operations, leaders can close the window attackers depend on. In cybersecurity, speed doesn’t just matter, it saves.
Cybersecurity is no longer just about prevention—it’s about rapid recovery and resilience!
Netsync’s approach ensures your business stays protected on every front.
We help you take control of identity and access, fortify every device and network, and build recovery systems that support the business by minimizing downtime and data loss. With our layered strategy, you’re not just securing against attacks—you’re ensuring business continuity with confidence.
Learn more about Netsync at www.netsync.com
Artificial Intelligence News & Bytes 🧠
Cybersecurity News & Bytes 🛡️
Time to change compliance forever.
We’re thrilled to announce our $32M Series A at a $300M valuation, led by Insight Partners!
Delve is shaping the future of GRC with an AI-native approach that cuts busywork and saves teams hundreds of hours. Startups like Lovable, Bland, and Browser trust our AI to get compliant—fast.
To celebrate, we’re giving back with 3 limited-time offers:
$15,000 referral bonus if you refer a founding engineer we hire
$2,000 off compliance setup for new customers – claim here
A custom Delve doormat for anyone who reposts + comments on our LinkedIn post (while supplies last!)
Thank you for your support—this is just the beginning.
👉 Get started with Delve
AI Power Prompt
This prompt that will assist leaders at an organization determine a cohesive strategy to use the velocity of patching for their benefit.
#CONTEXT:
Adopt the role of an expert in vulnerability management and executive cyber strategy. Create a framework to help leaders leverage patch velocity—the speed of vulnerability remediation—as a driver for resilience, compliance, and risk reduction. Explain why it matters, how to measure it, and how to make it a key performance metric.
#GOAL:
Guide leaders to:
Understand patch velocity and its business value
Measure and benchmark current performance
Link patch speed to reduced risk and improved posture
Develop a strategy that aligns patching priorities with business objectives and threat intelligence
#RESPONSE GUIDELINES:
Define Patch Velocity in Business Terms
Explain its role in reducing the “window of vulnerability” and MTTR.
Use examples of breaches caused by slow patching (e.g., Equifax, WannaCry).
Identify Influencing Factors
Asset inventory, scan frequency, threat intel integration, operational downtime.
Measure & Benchmark
Track MTTR for critical vulnerabilities.
Compare to industry benchmarks/regulatory requirements.
Strategic Benefits
Reduced exploit risk, faster compliance, improved trust, stronger cyber insurance profile.
Acceleration Roadmap
Automation, severity tiers with SLAs, intelligence-led prioritization, continuous validation.
Operationalize Patch Velocity
Include in executive dashboards, tie to team incentives, publish metrics when appropriate.
Leadership Recommendations
Prioritize budget, emergency zero-day policy, IT/security collaboration, quarterly KPI review.
Optional: Add a Patch Velocity Maturity Model from Ad-hoc → Optimized.
#INFORMATION ABOUT ME:
My organization: [DESCRIBE YOUR ORGANIZATION]
Industry: [INDUSTRY]
Current patching process: [CURRENT PATCH PROCESS]
Avg. patch timeline: [DAYS/WEEKS FOR CRITICAL PATCHES]
#OUTPUT:
Deliver a leadership-ready strategy including:
Plain-language explanation & business impacts
Benchmark metrics & KPIs
Roadmap to improve patch speed
Executive recommendations & one-page checklist
Tone should be strategic, business-focused, and action-oriented for non-technical leaders.
Questions, Suggestions & Sponsorships? Please email: [email protected]
Also, you can follow me on X (Formerly Twitter) @mclynd for more cybersecurity and AI.

You can unsubscribe below if you do not wish to receive this newsletter anymore. Sorry to see you go, we will miss you!











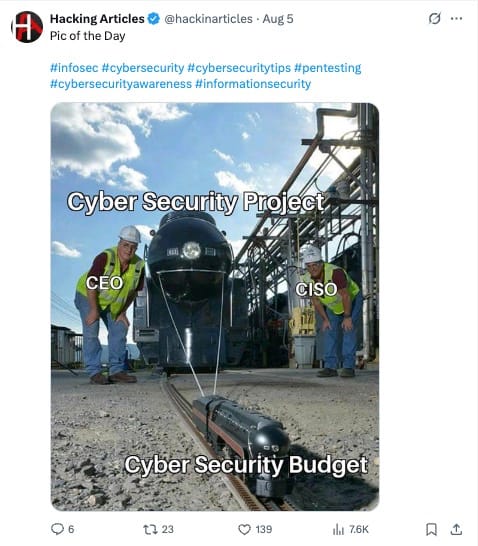
Social Media Image of the Week