
We are sitting at the intersection of cybersecurity and artificial intelligence in the enterprise, and there is much to know and do. Our goal is not just to keep you updated with the latest AI, cybersecurity, and other crucial tech trends and breakthroughs that may matter to you, but also to feed your curiosity.
Thanks for being part of our fantastic community!
In this edition:
Did You Know - Shadow AI
Article - Shadow AI in the Enterprise
Cybersecurity News & Bytes
AI Power Prompt
Social Media Image of the Week
Did You Know - Shadow AI
Did you know nearly 50% of all employees use shadow AI tools (i.e., non-company-issued or unapproved AI apps)? Source: Software AG study.
Did you know a recent enterprise survey found 90% of IT leaders are concerned about shadow AI from a privacy and security standpoint, with 46% extremely worried? Source: Komprise IT Survey.
Did you know 79% of IT leaders report their organization has experienced negative outcomes from employee use of AI tools (e.g., PII leakage, inaccurate results)? Source: Komprise IT Survey.
Did you know 13% of enterprises say shadow AI has already caused financial, customer or reputational damage? Source: Komprise IT Survey.
Did you know 60% of employees are using unapproved AI tools more than they did a year ago? Source: APMdigest / ManageEngine survey.
Did you know 93% of employees admit to inputting information into AI tools without approval? Source: HelpNetSecurity article. Help Net Security
57% of employees worldwide hide their AI usage from their employer? Source: KPMG/University of Melbourne survey.
Did you know over one-third (38%) of employees say they have shared sensitive work-related information with AI tools without their employer’s permission? Source: IBM article on shadow AI.
Did you know enterprises found that 89% of AI usage is unmonitored or unknown to the organization, creating major blind spots? Source: Cybersecurity Magazine article

Shadow AI in the Enterprise
Shadow AI in the EnterpriseUnapproved tools and hidden models are creating new blind spots in security posture
Let’s be honest for a second. Everyone’s using AI at work right now. Some openly, some quietly under the radar. You’ve got marketing teams playing with chatbots to write copy, engineers testing AI coding tools, and sales reps pasting customer data into free “productivity assistants.” It’s happening everywhere. And most of the time, it’s not out of rebellion. It’s out of necessity.
People just want to get things done faster. Who can blame them? Workloads keep piling up. Deadlines get tighter. And AI feels like a lifeline. But here’s where it gets messy. When employees start using these tools without approval, something dangerous creeps into the organization. Something security leaders are starting to call shadow AI.
If that phrase sounds familiar, it’s because it’s the AI version of shadow IT, the old problem where people downloaded unapproved software or used personal devices for work. Only now, the stakes are higher. Because AI tools don’t just store data. They learn from it.
Imagine this. Someone on your finance team uploads a spreadsheet with sensitive client information into a free AI tool to help analyze trends. A few clicks later, that same data might be sitting somewhere in the tool’s training logs, completely outside your company’s control. No bad intentions. Just a good employee trying to work smarter. But the result? A privacy nightmare waiting to happen.
That’s the thing about shadow AI. It isn’t born from malice. It’s born from enthusiasm, curiosity, and the drive to do more with less. Which makes it even trickier to manage. Because how do you stop people from experimenting with something that genuinely helps them do their jobs better?
Security teams are scrambling to figure it out. Some are setting up AI usage policies. Others are deploying monitoring tools to detect suspicious API calls or data transfers. But honestly, technology alone won’t solve this one. The real fix starts with trust and transparency.
Leaders need to start talking openly about AI. Not just about the risks, but about the excitement too. When employees feel safe asking, “Hey, can I use this tool?” instead of sneaking it, that’s when progress happens.
The truth is, shadow AI isn’t going anywhere. It’s the natural side effect of innovation moving faster than policy. The goal isn’t to stop it. It’s to understand it, guide it, and make it safe.
So maybe the question isn’t, “How do we stop shadow AI?” Maybe it’s, “How do we bring it into the light?” Because once everyone’s playing on the same team—security, innovation, and trust included—that’s when AI stops being a threat and starts becoming what it was always meant to be. An advantage.
Cybersecurity is no longer just about prevention—it’s about rapid recovery and resilience!
Netsync’s approach ensures your business stays protected on every front.
We help you take control of identity and access, fortify every device and network, and build recovery systems that support the business by minimizing downtime and data loss. With our layered strategy, you’re not just securing against attacks—you’re ensuring business continuity with confidence.
Learn more about Netsync at www.netsync.com
Artificial Intelligence News & Bytes 🧠
Cybersecurity News & Bytes 🛡️
Free email without sacrificing your privacy
Gmail is free, but you pay with your data. Proton Mail is different.
We don’t scan your messages. We don’t sell your behavior. We don’t follow you across the internet.
Proton Mail gives you full-featured, private email without surveillance or creepy profiling. It’s email that respects your time, your attention, and your boundaries.
Email doesn’t have to cost your privacy.
AI Power Prompt
This prompt will assist leaders in combating Shadow AI for their organization
#CONTEXT:
Adopt the role of an AI governance and cybersecurity strategist with expertise in Shadow AI detection, control, and policy development. You will help organizational leaders develop a strategy to identify, mitigate, and manage Shadow AI made up of unauthorized or unsanctioned use of AI tools, models, or APIs by employees or departments without oversight. The goal is to safeguard data, ensure compliance, and maintain responsible AI use without stifling innovation.
#GOAL:
You will create a Shadow AI Risk Management Framework that enables leaders to uncover hidden AI usage, assess its risks, and implement governance, monitoring, and awareness measures to ensure all AI activities align with enterprise standards.
#RESPONSE GUIDELINES:
Follow the steps below:
Identify Shadow AI Risks and Sources
Define what constitutes Shadow AI within the organization.
Map potential sources (e.g., employees using ChatGPT, third-party AI tools, or self-built models without approval).
Risk & Impact Assessment
Assess data privacy, security, IP leakage, and compliance risks from Shadow AI activities.
Prioritize risks based on likelihood and potential damage.
Detection & Monitoring Mechanisms
Recommend AI usage audits, network traffic analysis, and data access logs to detect unapproved tools.
Integrate AI discovery and monitoring tools across systems and endpoints.
Governance & Policy Enforcement
Develop a clear AI usage policy that defines permissible tools and procedures for approval.
Establish roles and accountability for AI oversight.
Create a formal risk assessment process for any new AI implementation.
Training & Culture Shift
Educate employees on the risks of Shadow AI and importance of compliance.
Foster a culture of transparency and safe AI experimentation under proper governance.
Innovation Enablement
Provide secure, approved AI sandboxes or internal LLM environments for innovation.
Balance control with flexibility to encourage responsible AI-driven productivity.
#INFORMATION ABOUT ME:
My organization: [ORGANIZATION NAME]
Industry sector: [INDUSTRY SECTOR]
Size of organization: [ORGANIZATION SIZE]
Current AI usage policies: [CURRENT AI POLICY STATUS]
Known or suspected Shadow AI issues: [SHADOW AI ISSUES]
Compliance and regulatory obligations: [COMPLIANCE REQUIREMENTS]
#OUTPUT:
Deliver a Shadow AI Control Strategy Report that includes:
Definition and scope of Shadow AI for the organization
Risk and impact assessment matrix
Governance and detection framework
Awareness and training plan
Innovation-friendly policy recommendations
Questions, Suggestions & Sponsorships? Please email: [email protected]
Also, you can follow me on X (Formerly Twitter) @mclynd for more cybersecurity and AI.

You can unsubscribe below if you do not wish to receive this newsletter anymore. Sorry to see you go, we will miss you!










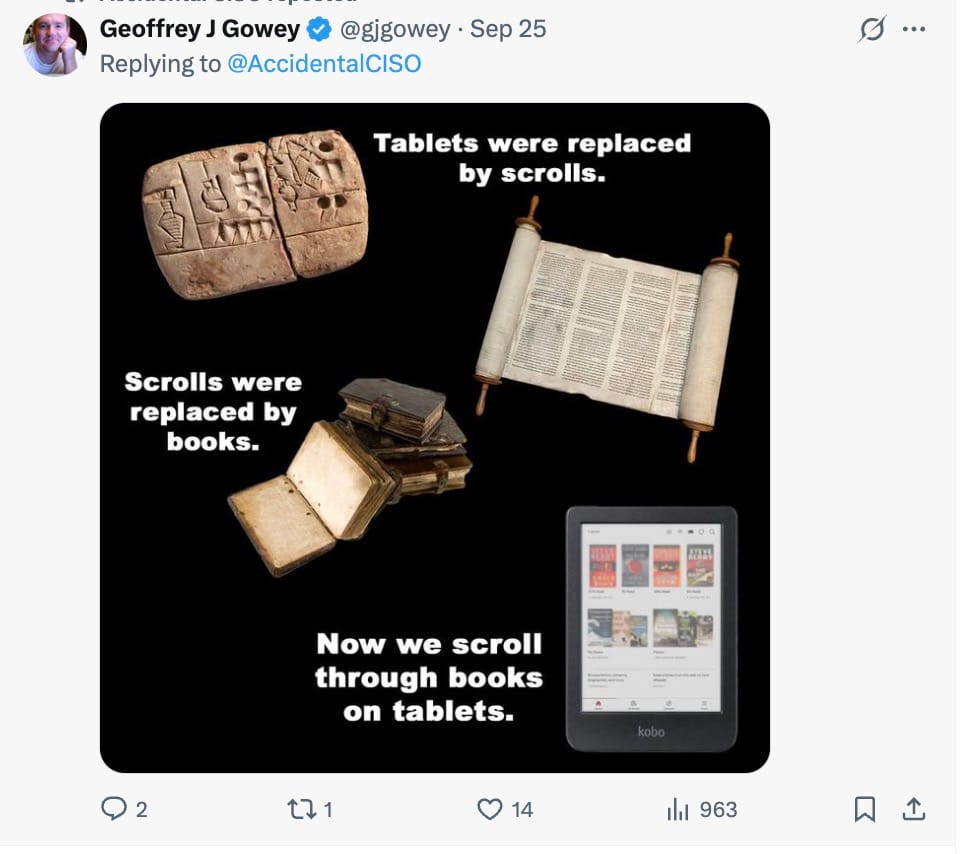
Social Media Post